What is Digital Fraud and How to Prevent it?
29 May 2025 • 10 min read
What is Digital Fraud and How to Prevent it?
29 May 2025 • 10 min read
Digital fraud involves deceptive tactics used in online spaces to steal money, personal data, or access to systems. As more activity moves online, fraud is becoming more widespread and sophisticated. In 2024, global e-commerce fraud alone resulted in an estimated $48 billion in losses, reflecting how serious and costly this threat has become.
From phishing emails to AI-generated scams, digital fraud targets both individuals and organizations, causing financial damage and undermining trust. This article outlines the common forms of digital fraud, how they operate, and the steps businesses can take to prevent them.
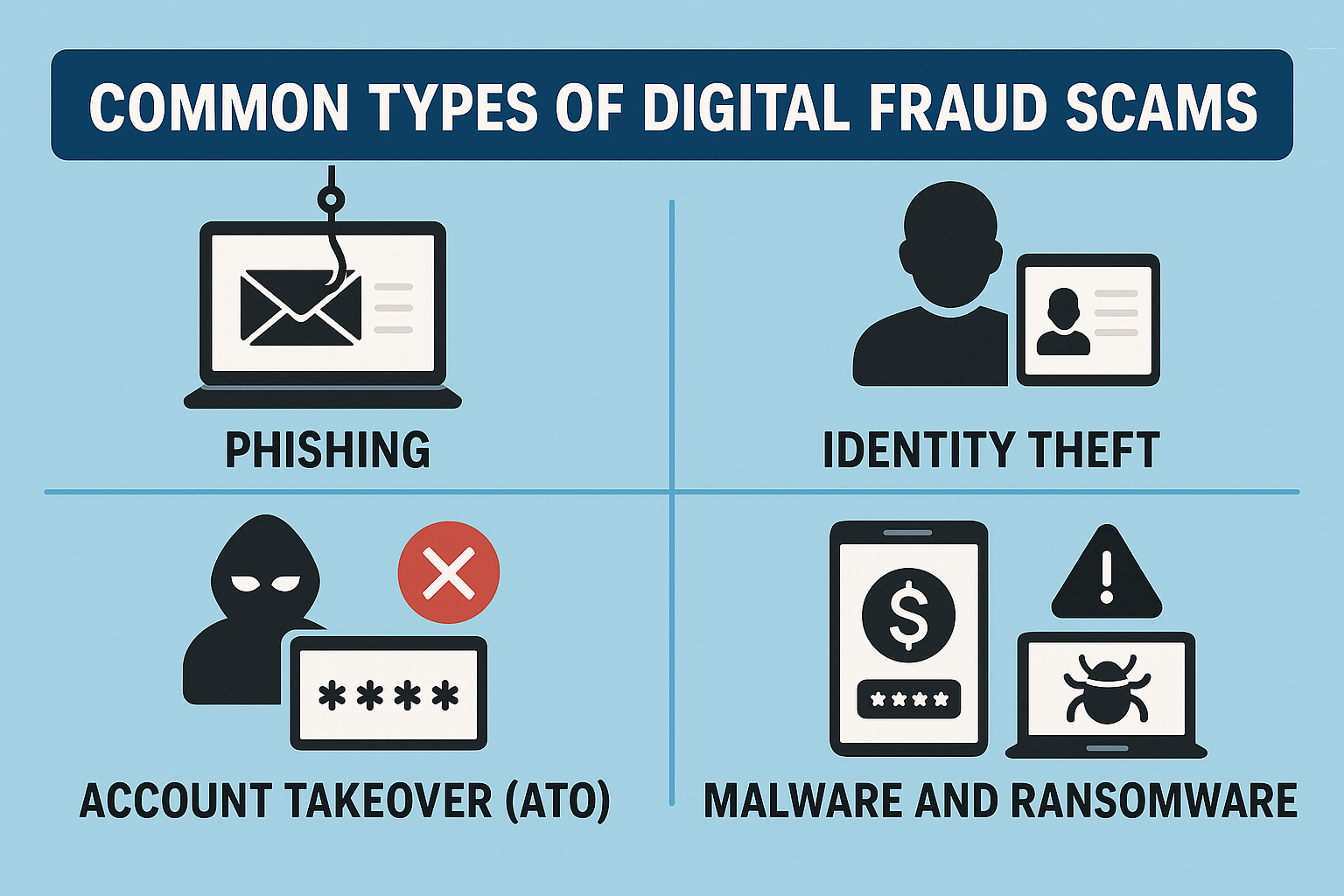
Common Types of Digital Fraud Scams
Digital fraud manifests in various forms, each leveraging unique tactics to exploit victims. Below are some of the most common types:
1. Phishing and Social Engineering
Phishing involves cybercriminals sending fraudulent emails, text messages, or other communications that appear to come from legitimate sources. These messages trick users into providing sensitive information, such as login credentials or financial details, or clicking on malicious links that install malware. For example, a fake login page mimicking a bank’s website can capture a user’s credentials, while fraudulent customer service texts may prompt users to disclose personal information. Social engineering, a broader tactic, manipulates human psychology to bypass security measures.
2. Identity Theft
Identity theft occurs when fraudsters steal personal information, such as names, Social Security numbers, or credit card details, to impersonate victims. This stolen data can be used to open fraudulent accounts, make unauthorized purchases, or access existing accounts. For instance, cybercriminals may use stolen credentials to drain bank accounts or apply for loans in the victim’s name.
3. Payment Fraud
Payment fraud involves unauthorized transactions or manipulation of payment systems. Common examples include credit card fraud, where stolen card details are used for purchases, and chargeback scams, where fraudsters dispute legitimate transactions to receive refunds. Fake invoices sent to businesses or individuals also fall under this category, tricking victims into paying for nonexistent services.
4. Account Takeover (ATO)
Account takeover happens when cybercriminals gain unauthorized access to user accounts, often through stolen credentials or brute force attacks. Techniques like credential stuffing, using leaked usernames and passwords from one platform to access others, are prevalent. Once inside, fraudsters may change account details, make unauthorized transactions, or steal sensitive data.
5. Malware and Ransomware
Malware is a broad category of malicious software that includes viruses, spyware, and keyloggers. It is designed to infiltrate systems, steal sensitive data, or disrupt normal operations. Ransomware, a particularly harmful type of malware, prevents users from accessing their systems or encrypts their data, then demands payment to restore access. These attacks can cause serious harm to both businesses and individuals, leading to financial losses, operational disruptions, and reputational damage.
6. Other Emerging Threats
As technology evolves, so do fraud tactics. Deepfake scams use AI-generated videos or audio to impersonate trusted individuals, tricking victims into transferring money or sharing data. Cryptocurrency fraud, such as fake investment schemes or wallet hacks, has also surged with the rise of digital currencies.
How Digital Fraud Works?
Digital fraud often follows a calculated sequence of actions, where attackers use social and technical strategies to exploit both systems and users. The process typically begins with the selection of victims, who may be chosen based on their online behavior, financial status, or security posture. Attackers then craft deceptive communications, posing as legitimate organizations like banks or service providers to earn the target's trust. Once engagement is established, they find ways to infiltrate systems—this could involve bypassing weak authentication, exploiting software flaws, or manipulating employees.
Victims may be misled into performing risky actions such as clicking malicious links, approving fake invoices, or installing harmful apps. The stolen data, including account credentials and payment information, is then turned into profit through various channels such as unauthorized purchases, resale on black markets, or ransom demands. Throughout the process, fraudsters work to obscure their identity and actions by using tools that mask their digital footprint, making it harder for organizations to detect and respond to the threat.
The Impact of Digital Fraud on Business
Digital fraud poses a serious threat to businesses, leading to both immediate financial losses and long-term reputational damage. Companies may face direct costs such as stolen funds, chargebacks, legal penalties, and incident response expenses. However, the broader consequences can be even more damaging: customer trust erodes, brand reputation suffers, and relationships with partners and stakeholders are strained. Operational disruptions caused by fraud investigations or compromised systems can slow productivity and divert resources from core business functions. Additionally, businesses operating in highly regulated industries may face compliance risks and increased scrutiny following a breach. In an era where digital interactions dominate, even a single incident of fraud can have a ripple effect that undermines customer confidence and weakens competitive standing.
Emerging Trends in Digital Fraud for 2025
As digital ecosystems evolve, fraudsters are exploiting advanced technologies and new vulnerabilities. Below are the key trends driving digital fraud in 2025:
- AI-Powered Fraud Attacks: Generative AI is enabling fraudsters to craft highly convincing phishing emails, deepfake videos, and voice scams. These tools mimic trusted entities with precision, challenging both user vigilance and traditional security measures.
- Rise of Synthetic Identity Fraud: By blending stolen and fabricated data, criminals create synthetic identities to open fraudulent accounts, secure loans, or bypass identity verification. The abundance of leaked data on the dark web fuels this trend.
- IoT Device Exploitation: The growing use of Internet of Things (IoT) devices, like smart home systems and wearables, introduces new vulnerabilities. Fraudsters target unsecured devices to access networks or steal sensitive data.
- Cryptocurrency and DeFi Exploits: Decentralized finance (DeFi) platforms and crypto exchanges face escalating threats from rug pulls, phishing, and smart contract vulnerabilities. Social engineering and insider collusion amplify these risks.
- Real-Time Payment Scams: The global shift to instant payment systems has spurred authorized push payment (APP) fraud, where victims are deceived into transferring funds. The speed of these transactions limits detection opportunities.
- Insider Fraud and Collusion: Internal actors, such as employees or contractors, increasingly exploit system access to facilitate fraud. Collusion with external fraudsters heightens the risk of data breaches and financial losses.
Advanced Defense Strategies Against Digital Fraud
1. Implement Robust Authentication Protocols
Strengthening authentication mechanisms is a foundational step in preventing digital fraud. Organizations should adopt multi-factor authentication (MFA), behavioral biometrics, and CAPTCHA technologies to verify user identities and mitigate the risk of unauthorized access. These methods add multiple layers of security that go beyond traditional username and password combinations, making it significantly harder for attackers to compromise accounts.
2. Establish Real-Time Threat Detection and Monitoring
Deploying real-time monitoring systems equipped with artificial intelligence and machine learning enables early detection of fraudulent activities. These tools can analyze user behavior, detect anomalies, and trigger alerts when suspicious actions occur. Timely intervention, supported by automated or human responses, can prevent minor incidents from escalating into major breaches.
3. Promote a Security-Conscious Culture through Education
Human error remains one of the leading causes of successful fraud attempts. Businesses must invest in continuous cybersecurity training for employees at all levels. Training should focus on recognizing phishing schemes, avoiding unsafe online behavior, and understanding the latest social engineering tactics. An informed workforce serves as a strong first line of defense against digital fraud.
4. Enforce Rigorous Data Protection and Access Control
Sensitive information should be safeguarded through comprehensive encryption protocols, both in storage and during transmission. Access to critical systems and data must be granted based on clearly defined user roles and responsibilities, following the principle of least privilege. Regular reviews of access rights help ensure that only authorized personnel have entry to high-risk environments.
5. Conduct Routine Security Audits and Risk Assessments
Proactive auditing and vulnerability assessments are essential to uncover and address security weaknesses. Through penetration testing, system reviews, and compliance checks, organizations can identify exploitable gaps and take corrective actions before adversaries can take advantage. These assessments also ensure alignment with regulatory standards and industry best practices.
6. Collaborate with Reputable Cybersecurity Partners
Staying ahead of evolving threats requires continuous adaptation and external expertise. Partnering with trusted cybersecurity vendors and solution providers gives businesses access to advanced tools, threat intelligence, and professional guidance. Regular consultation with experts helps refine security strategies and enhances the overall resilience of digital infrastructure.
How GeeTest Safeguards Enterprises from Digital Fraud?
GeeTest offers an advanced bot mitigation and user verification solution that plays a critical role in helping businesses combat digital fraud. By leveraging a combination of behavioral biometrics, AI-driven risk analysis, and adaptive verification mechanisms, GeeTest provides multi-layered protection against fraudulent activities such as credential stuffing, account takeovers, and automated bot attacks.
At the core of GeeTest’s solution is its adaptive CAPTCHA technology, which analyzes over 200 behavioral data points—such as mouse movements, click patterns, and interaction speed—to distinguish between human users and malicious bots in real time. Unlike static CAPTCHAs, GeeTest's system adapts dynamically based on the threat level, delivering a seamless user experience for legitimate users while presenting robust challenges to suspicious ones.
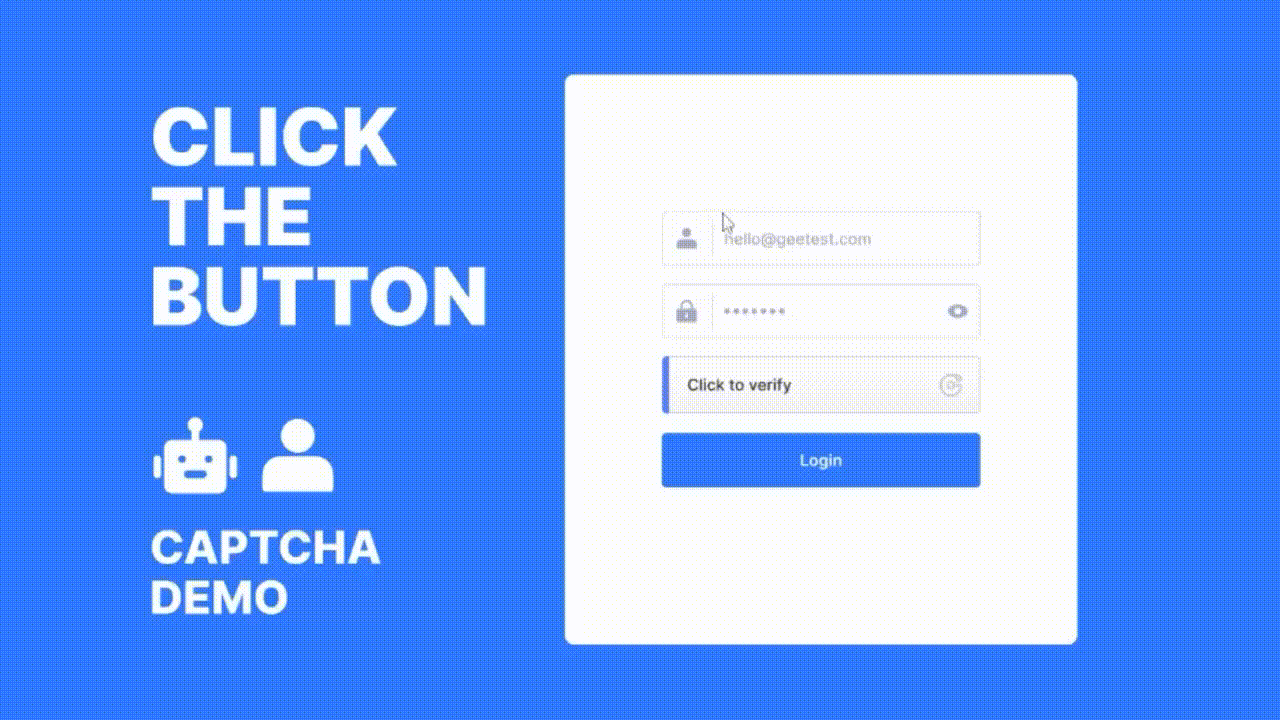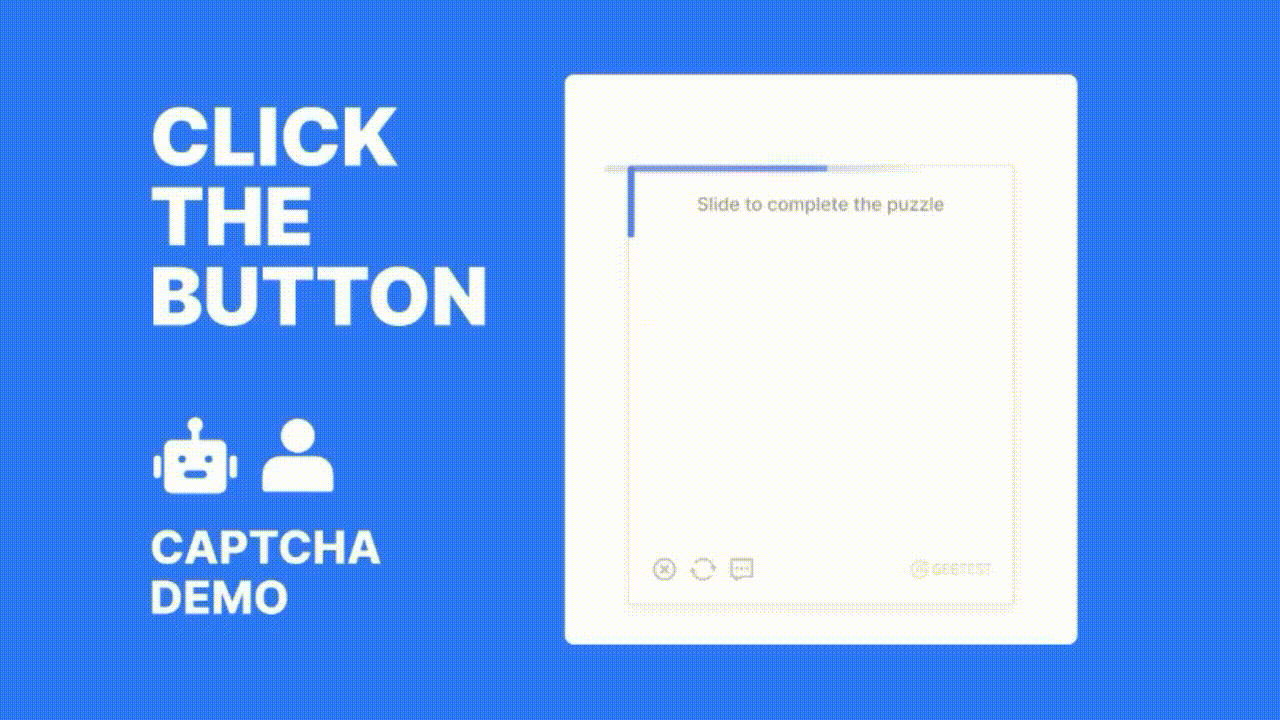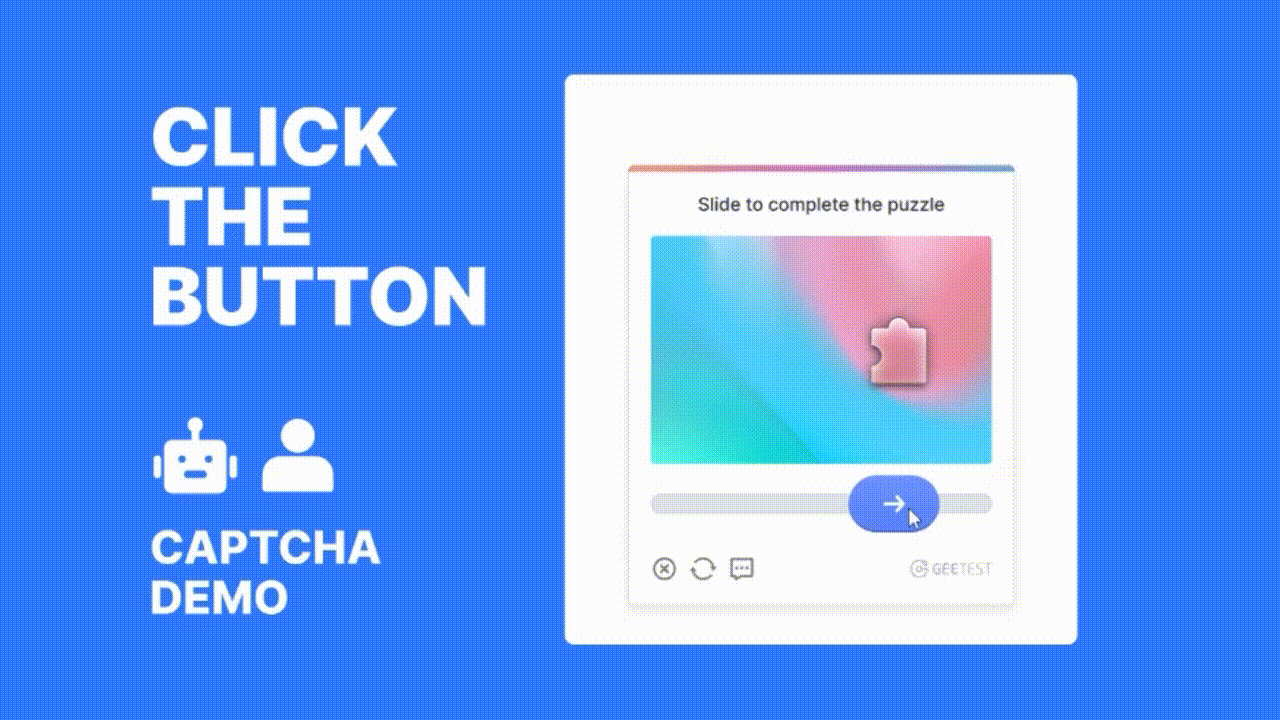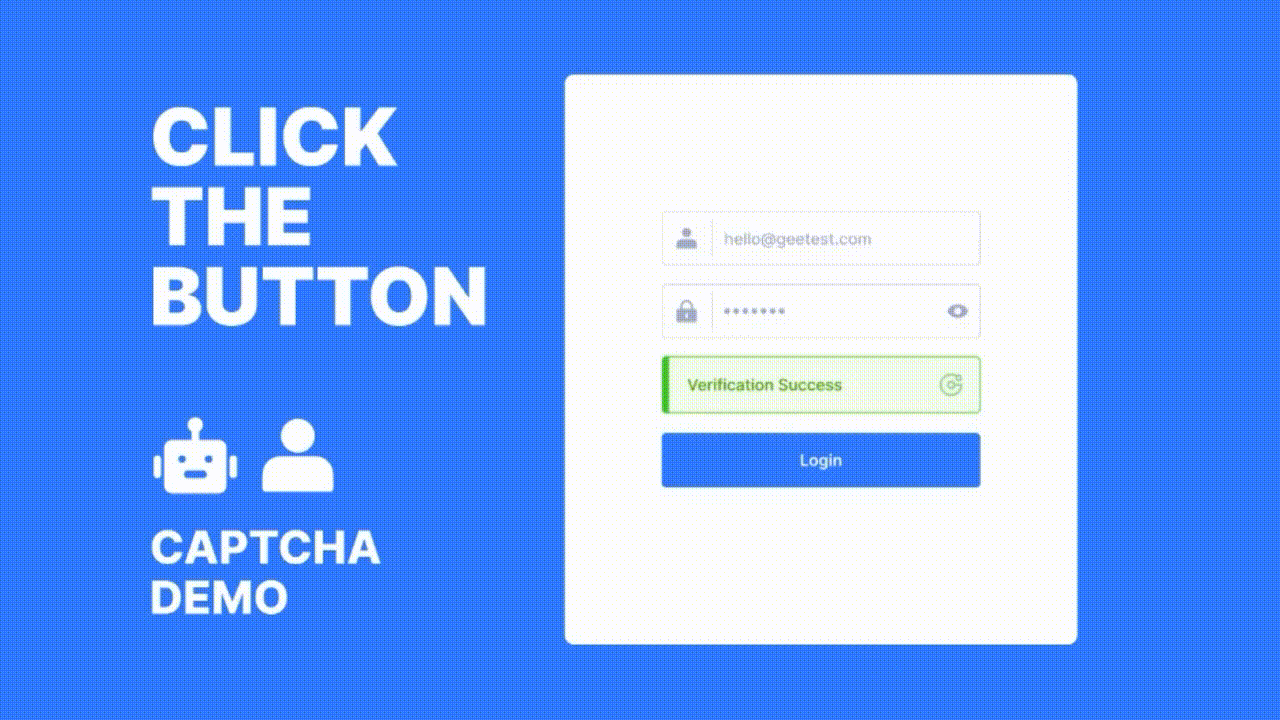
GeeTest also offers risk-based verification, meaning users identified as high-risk are subjected to more rigorous checks, while low-risk users experience minimal friction. This approach enhances both security and user experience, reducing abandonment rates often caused by traditional verification methods.
In addition, GeeTest provides detailed threat intelligence and analytics dashboards, enabling businesses to monitor traffic patterns, identify attack sources, and fine-tune their defenses accordingly. This transparency empowers organizations to make informed decisions and stay ahead of emerging fraud tactics.
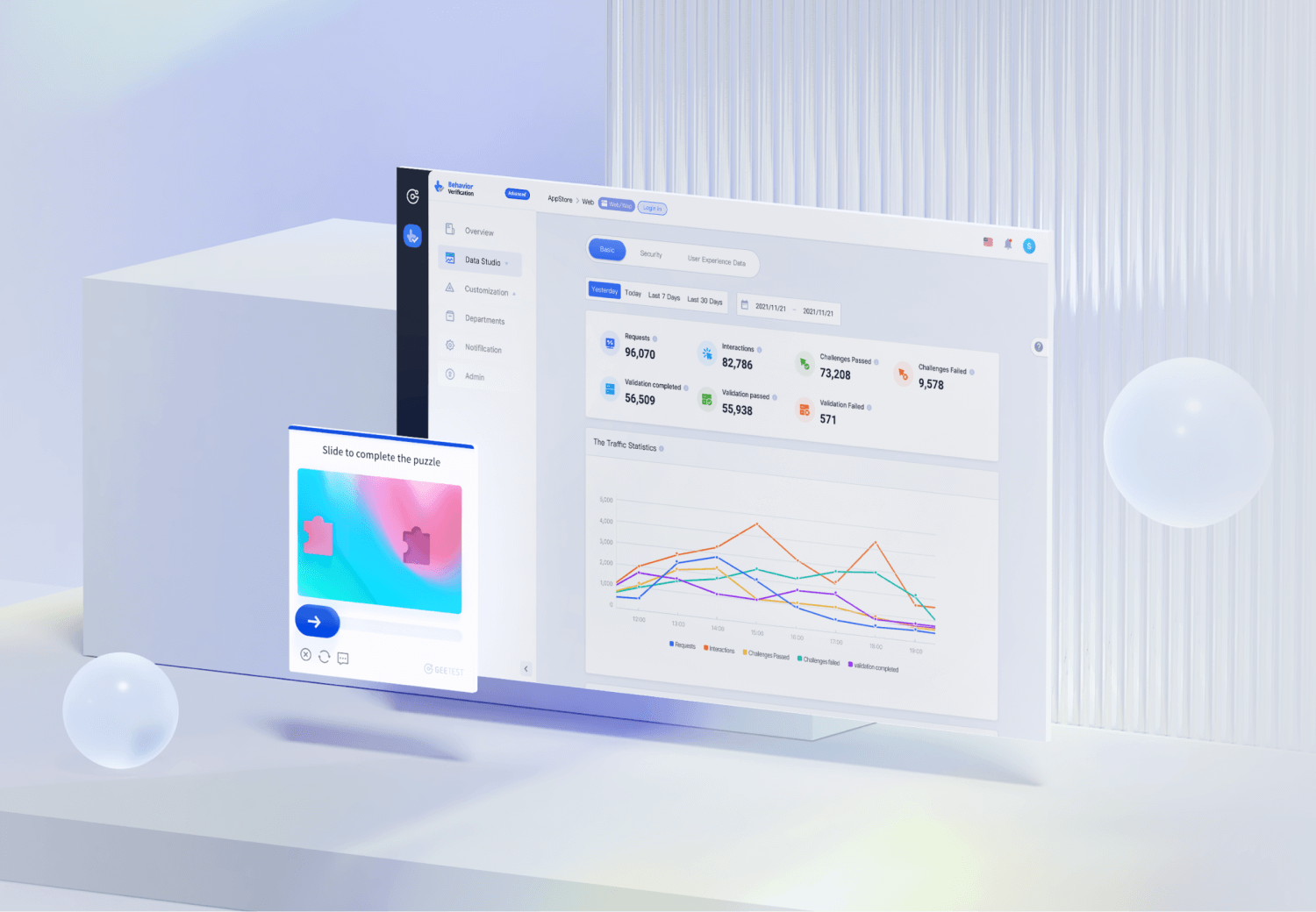
By integrating GeeTest into login portals, registration forms, and payment pages, businesses can significantly reduce exposure to automated fraud attempts and unauthorized access. As digital fraud techniques continue to evolve, GeeTest stands out as a proactive and intelligent solution designed to safeguard digital assets, preserve user trust, and ensure operational continuity.
Conclusion
Digital fraud is an ever-evolving threat that takes advantage of the interconnected nature of today’s technology. Its many forms, from phishing to ransomware, can lead to serious consequences including financial loss, data breaches, and reputational damage. Combating this threat requires a proactive and multi-layered approach.
By combining individual awareness, strong organizational policies, advanced tools like GeeTest CAPTCHA, and adherence to regulatory standards, we can significantly reduce the risk. Simple measures such as creating strong passwords, enabling multi-factor authentication, staying informed about fraud tactics, and implementing robust cybersecurity practices are key. In a world that relies heavily on digital infrastructure, prevention is not optional — it is essential to protecting our future.
GeeTest
GeeTest
Subscribe to our newsletter