What is SMS Pumping and How Does It Work in 2025
08 Aug 2025 • 10 min read
What is SMS Pumping and How Does It Work in 2025
08 Aug 2025 • 10 min read
You face a growing threat in 2025 called SMS Pumping. Attackers use automated tools to exploit SMS-based systems, causing real financial harm. For example, Twitter loses about $60 million each year when attackers trigger fake SMS messages for authentication. Many industries, especially those relying on SMS for verification, have seen millions in losses. SMS Pumping not only drains money but also disrupts operations and puts your users at risk.
Key Takeaways
- SMS Pumping is a scam where attackers use bots to trigger many fake SMS messages, causing high costs and service disruptions.
- Attackers exploit SMS systems by sending repeated requests to premium-rate numbers, making your business pay inflated charges.
- Common targets include SMS-based one-time passcodes (OTPs) and automated responses like appointment confirmations.
- Detect SMS Pumping by monitoring sudden spikes in SMS traffic, repeated requests from similar numbers, and unusual locations.
- Use CAPTCHA and advanced bot detection tools to block automated attacks effectively.
- Implement rate limiting to restrict how many SMS messages a user or device can request in a short time.
- Secure your SMS APIs by checking for risky numbers and blocking suspicious requests before sending messages.
- Build a multi-layered defense combining real-time monitoring, AI detection, bot mitigation, and strong partnerships with trusted providers like GeeTest.
What is SMS Pumping
Definition
You may hear about SMS Pumping as a scam that targets businesses and users who rely on SMS for security and communication. In this scheme, fraudsters register premium-rate phone numbers through questionable telecom providers. They then use automated tools to send repeated login or verification requests. Each request triggers an SMS message, often for two-factor authentication or account verification. The service provider pays for each SMS sent, and the scammers collect a share of the charges. This method does not have a formal definition from cybersecurity authorities, but experts describe it as a way to abuse SMS-based systems for profit.
Alternate Names
You might see SMS Pumping called by other names in the telecommunications industry. These terms all describe similar fraudulent activities:
- SMS toll fraud
- Artificially Inflated Traffic (AIT) fraud
These names highlight the main goal of the scam: to create fake SMS traffic and generate illegal revenue. The attackers use the same tactics to trick businesses into sending large volumes of SMS messages to numbers they control.
Why It Matters
SMS Pumping poses a serious threat to your business and your users in 2025. Attackers use bots to flood SMS systems with fake requests. They exploit automatic SMS sending features, such as one-time passcodes (OTPs) and appointment confirmations. This attack can cause major financial losses. For example, Twitter lost about $60 million each year because of SMS Pumping. Sectors like banking, e-commerce, and healthcare face even greater risks. Attackers can overwhelm OTP and confirmation systems, leading to service disruptions and higher costs.
You must stay alert and use strong defenses. Regular monitoring, employee training, and up-to-date security tools are key to stopping SMS Pumping before it causes damage.
How SMS Pumping Works
Attack Methods
Bots and Scripts
Attackers use bots and automated scripts to launch SMS Pumping attacks. You may notice that these bots target phone number input fields on websites and apps. When a bot fills out these forms with fake or sequential phone numbers, it triggers the system to send one-time passcodes (OTPs) or other SMS content. This process creates a flood of SMS messages, overwhelming both the recipient's device and your messaging infrastructure.
- Bots fill out online forms with fake or sequential phone numbers.
- The system sends a large volume of SMS messages to these numbers.
- This flood causes delays for real users and increases your SMS costs.
- Attackers use this method to disrupt services, drain prepaid accounts, or intercept sensitive information.
- Bots bypass normal user interaction, making it hard to spot the attack right away.
Premium-Rate Numbers
Fraudsters often register premium-rate or high-cost phone numbers through certain mobile network operators. When your system sends SMS messages to these numbers, you pay a higher fee. Attackers receive a share of this revenue, turning your SMS system into a source of profit for them. They automate the process, sending thousands of messages to these numbers in a short time. This method not only increases your costs but also makes detection more difficult because the traffic looks like normal SMS activity.
Exploited Services
OTPs and App Links
You rely on SMS-based OTPs and app links for user authentication and onboarding. Attackers know this and target these endpoints. Bots flood your website or app with fake phone numbers, causing your system to send OTPs and app links to numbers controlled by fraudsters. These numbers often have similar or sequential patterns, such as ending in 1000, 1001, 1002, and so on. This pattern helps attackers automate the attack and maximize profits.
- Fraudsters use bots to send many fake OTP requests.
- These requests trigger OTPs or app links to be sent to their controlled numbers.
- The attack inflates your SMS traffic and costs.
- Monitoring for rapid OTP requests from similar phone numbers can help you detect this activity.
Automated Responses
Many businesses use automated SMS responses for appointment confirmations, password resets, or notifications. Attackers exploit these features by sending repeated requests, often through bots. Each request triggers an SMS, which adds to your operational costs and can disrupt service for real users. Automated responses are easy targets because they often lack strong verification checks.
Collusion and Coordination
Attackers do not work alone. They often coordinate with premium-rate number providers, especially certain mobile network operators. This collaboration allows them to send large volumes of SMS messages to premium numbers, inflating your costs. The attackers, MNOs, and sometimes third-party aggregators share the profits from these inflated charges. This setup resembles affiliate marketing, where fraudsters earn commissions for driving high SMS traffic.
Mobile network operators play a key role in SMS Pumping. Some MNOs have weak security or gaps in their registration processes, making it easier for attackers to exploit their systems. Reliable MNOs help prevent SMS Pumping by offering fraud detection tools and supporting rate limits. You should choose partners with strong security measures to reduce your risk.
Impact of SMS Pumping
Financial Loss
You face a real financial threat from SMS Pumping. In 2023, businesses around the world spent about $1.16 billion on fraudulent SMS messages. This number only covers direct costs, such as inflated SMS charges. When you add expenses for service interruptions, investigations, customer support, and reputation repair, the total loss grows even larger. Experts expect the global financial impact to reach several billion dollars in 2025. The Communications Fraud Control Association reported that telecom fraud caused $39 billion in losses in 2023, with SMS fraud making up a large part of that amount. If you run a business that relies on SMS for authentication or communication, you risk losing money every time attackers trigger fake messages. These losses can threaten your profits and even your ability to operate.
Operational Issues
SMS Pumping does not just drain your budget. It can also disrupt your daily operations. Attackers often use bots to flood your systems with fake SMS requests. For example, one attack used over 500 fake identities to target a company’s onboarding process, causing major service slowdowns. Twitter lost about $60 million each year because bots abused its two-factor authentication system. You might see your SMS services overloaded, which can force you to suspend them temporarily. This action blocks real customers from getting important messages.
- You may overspend on SMS without gaining real customers.
- Your team might need to spend extra time and money on new security tools.
- Customer service staff could get overwhelmed with complaints about failed messages.
- OTP fraud can lead to more login attempts with stolen credentials, raising your risk of data breaches.
A sudden spike in SMS traffic, especially from unusual locations or with similar phone numbers, often signals an attack. If you do not act quickly, you risk losing both money and customer trust.
User Disruption
Your users also suffer when SMS Pumping strikes. Attackers can send SMS messages to premium-rate numbers, causing your customers to face unexpected charges. Some users may even see their credit scores drop or their reputations damaged. Fraudsters sometimes trick users into signing up for costly services or clicking on dangerous links. These scams can expose users to phishing or malware attacks.
- Users may not receive important authentication codes on time.
- Service quality drops, leading to frustration and lost trust.
- Security risks increase as attackers try to steal personal information.
When your business faces SMS Pumping, your users may lose faith in your service. This loss of trust can hurt your brand and make it harder to keep loyal customers.
How to Detect SMS Pumping
Traffic Patterns
You can spot suspicious activity by watching for unusual traffic patterns in your SMS systems. Attackers often use bots or automated scripts to send rapid and repeated requests for OTPs or verification codes. These requests usually target a small set of phone numbers that fraudsters control. You may also notice:
- Sudden spikes in SMS request frequency
- High volumes of messages sent to a few numbers
- Use of proxies or VPNs to hide the true origin of requests
- Mismatches between claimed user locations and actual IP or phone number locations
- Bulk identical content sent in a short time
Behavioral analytics and device fingerprinting also help you find multiple fraudulent requests from the same source. AI-driven traffic analysis can flag messaging volumes that do not match normal user behavior. When you see a sudden increase in messages from a small region or specific service, you should investigate right away.
Anomaly Monitoring
You need strong anomaly monitoring to protect your SMS channels. Start by setting rate limits to restrict how many SMS messages a user or device can request in a short time. This step reduces the risk of automated abuse. Use machine learning algorithms to spot and block unusual authentication patterns as they happen. Here are some effective techniques:
- Rate limiting per user or per minute
- Real-time anomaly detection using machine learning
- Continuous monitoring and auditing of SMS traffic
- Geo-fencing to control SMS activity by location
- Device behavior analysis, such as checking for risky devices or repeated misuse
You can also use advanced methods like ARIMA or EWMA to find unusual spikes in SMS traffic. Training your employees to recognize signs of fraud adds another layer of defense.
Dashboard Tools
Modern dashboard tools give you real-time visibility into your SMS traffic. Solutions like GeeTest provide advanced bot detection and mitigation through products with intelligent dashboard. These tools monitor traffic, identify suspicious patterns, and use CAPTCHA challenges to block malicious activity. GeeTest offers a fraud management platform that detects bot traffic, flags risky devices, and checks device velocity. You get real-time alerts, sometimes even through GeeTest service team, so you can act fast.
With these dashboards, you can:
- Track SMS traffic in real time
- Detect abnormal spikes or bot-driven activity
- Respond quickly to prevent toll fraud
Prevention Strategies Against SMS Pumping
CAPTCHA Solutions
You can stop most automated attacks by adding CAPTCHA solutions to your signup and login forms. CAPTCHA tools, such as GeeTest CAPTCHA, use challenge-response steps to block bots while letting real users pass. These systems spot suspicious activity and present extra challenges that confuse bots. This method forms part of a layered defense, working with rate limiting and device checks to keep your SMS channels safe.
GeeTest CAPTCHA
GeeTest CAPTCHA stands out for its advanced features that fight automated attacks. You get more than just a simple puzzle. GeeTest uses behavioral biometrics and dynamic security methods to spot bots and block them before they trigger SMS messages. The system checks user actions, like mouse movement and typing speed, to tell humans from bots. After a user completes the CAPTCHA, GeeTest adds a second server-side check to confirm the user is real before sending any SMS.

Rate Limiting
You can slow down or block attacks by setting limits on how many SMS messages a user or device can request. Rate limiting stops bots from sending thousands of requests in a short time. You should:
- Set a maximum number of SMS requests per user or IP address within a set period.
- Add delays between repeated requests to make attacks less effective.
- Watch for patterns, such as many requests from the same device or location.
Secure APIs
You must secure your APIs to prevent attackers from abusing your SMS services. Modern fraud detection APIs, check for risk factors such as SIM swapping, trusted network status, and call forwarding. These APIs let you set risk thresholds and block suspicious numbers before sending SMS messages.
- Add CAPTCHA or bot detection to all forms that trigger SMS.
- Limit the number of SMS messages sent to each phone number.
- Introduce delays between verification attempts.
- Block SMS to countries where you do not operate.
- Check carrier information to avoid sending SMS to premium or risky numbers.
- Ask for more user information, not just a phone number, to stop bots.
- Consider using other forms of authentication, since SMS OTPs have known risks.
Choosing SMS Pumping Protection Tools
To effectively defend against SMS Pumping fraud, selecting the right tool is critical. The tool you choose should solve two core problems: early detection of fraudulent activity and real-time prevention before damage occurs.
What to Look For
When evaluating solutions, focus on tools that offer:
- Pre-send risk scoring using machine learning
- Real-time API integration for instant detection and blocking
- Low latency, high accuracy in identifying suspicious SMS traffic
- Device fingerprinting and behavioral analysis
- CAPTCHA and anti-bot protections
- Real-time dashboards to monitor attacks and visualize cost savings
- Global compatibility with any SMS provider
- Compliance with regulations and fraud insurance
Best Solution Recommendation
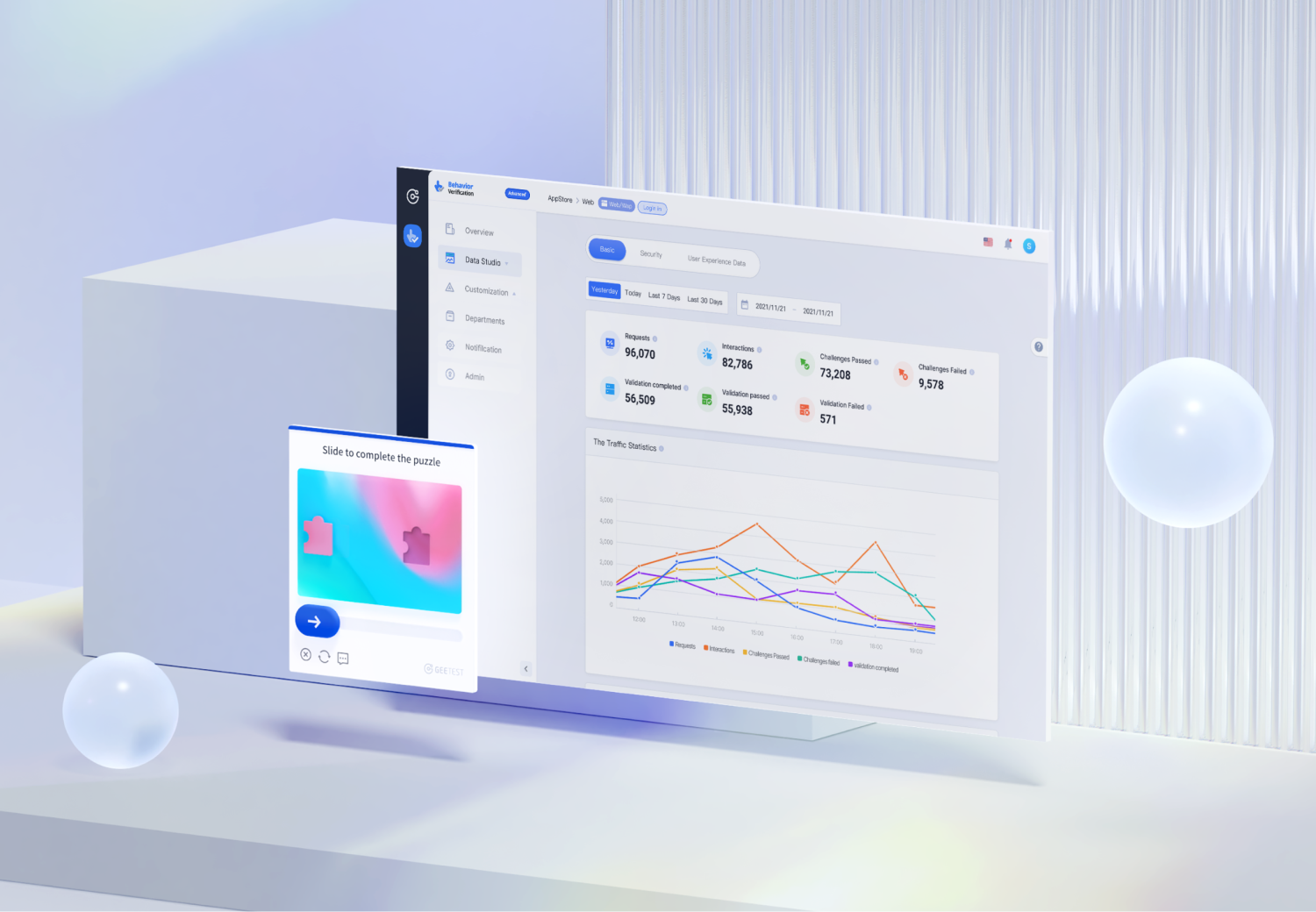
When it comes to defending against SMS Pumping attacks, GeeTest Bot Management Platform stands out as a comprehensive, flexible, and high-performance solution. It’s purpose-built to meet the exact needs listed above, offering a multi-layered defense that works in real time.
- Advanced CAPTCHA & Device Fingerprinting & BRDE: GeeTest combines its next-gen CAPTCHA, device fingerprinting, and Business Rules Decision Engine (BRDE) to flag and block risks before an SMS is sent. This allows you to block suspicious requests instantly—not after the damage is done.
- Flexible for Startups, Powerful for Enterprises: Whether you're a startup needing lightweight integration or building a full-scale risk control system, GeeTest adapts to your architecture and risk profile.
- Real-Time Risk Assessment with Low Latency: GeeTest’s intelligent engine processes and evaluates risk in milliseconds, supporting instant SMS delivery decisions without slowing down your system.
- Seamless API Integration: Easily integrates into your backend systems and SMS flows with stable APIs, enabling real-time protection and adaptive response logic.
- Dashboards for Monitoring & Analytics: Provides intuitive, real-time dashboards so you can track attack patterns, monitor cost impact, and fine-tune policies.
- Global Reach, Cross-Platform Compatibility: Supports any SMS provider and scales globally, making it ideal for businesses expanding into new markets or operating at enterprise scale.
- Protection Against Automation & Bots: Its CAPTCHA technology is bot-resistant by design, stopping automated SMS abuse at the source—before any cost is incurred.
GeeTest is more than just a CAPTCHA—it’s an intelligent risk decision platform that protects your business from SMS Pumping with speed, precision, and scalability. If you're serious about stopping SMS fraud before it impacts your bottom line, GeeTest is the solution of choice.
.png)
FAQ
What is SMS Pumping in simple terms?
You face SMS Pumping when attackers use bots to trigger many fake SMS messages. They do this to make money from premium-rate numbers. Your business pays for these messages, and scammers collect the profits.
How can I tell if my business is under SMS Pumping attack?
You may notice sudden spikes in SMS traffic, many requests from similar phone numbers, or messages sent to unusual locations. Monitoring your SMS dashboard helps you spot these signs early.
Why do attackers use premium-rate numbers?
Attackers use premium-rate numbers because each SMS sent to these numbers costs more. They get a share of the extra charges. This method turns your SMS system into a source of income for them.
Can CAPTCHA really stop SMS Pumping?
Yes. CAPTCHA blocks most bots from sending fake SMS requests. Advanced solutions like GeeTest CAPTCHA use behavior analysis to tell humans from bots, making your SMS system much safer.
GeeTest
GeeTest
Subscribe to our newsletter