Increasing the Cost of Cracking to Reduce Cyber Attacks
03 Feb 2023 • 10 min read
Increasing the Cost of Cracking to Reduce Cyber Attacks
03 Feb 2023 • 10 min read
Cyber attacks are a constant threat, affecting organizations of all sizes and industries on a daily basis. Cybersecurity risks have been on a rise, and according to the 2022 Cybersecurity Ventures report, the number of cyber attacks is expected to increase by 15% each year, with the total cost of cybercrime reaching $7 trillion by 2022. And this figure is predicted to grow to $10.5 trillion in 2025. This means that organizations need to be prepared to protect themselves from these threats.
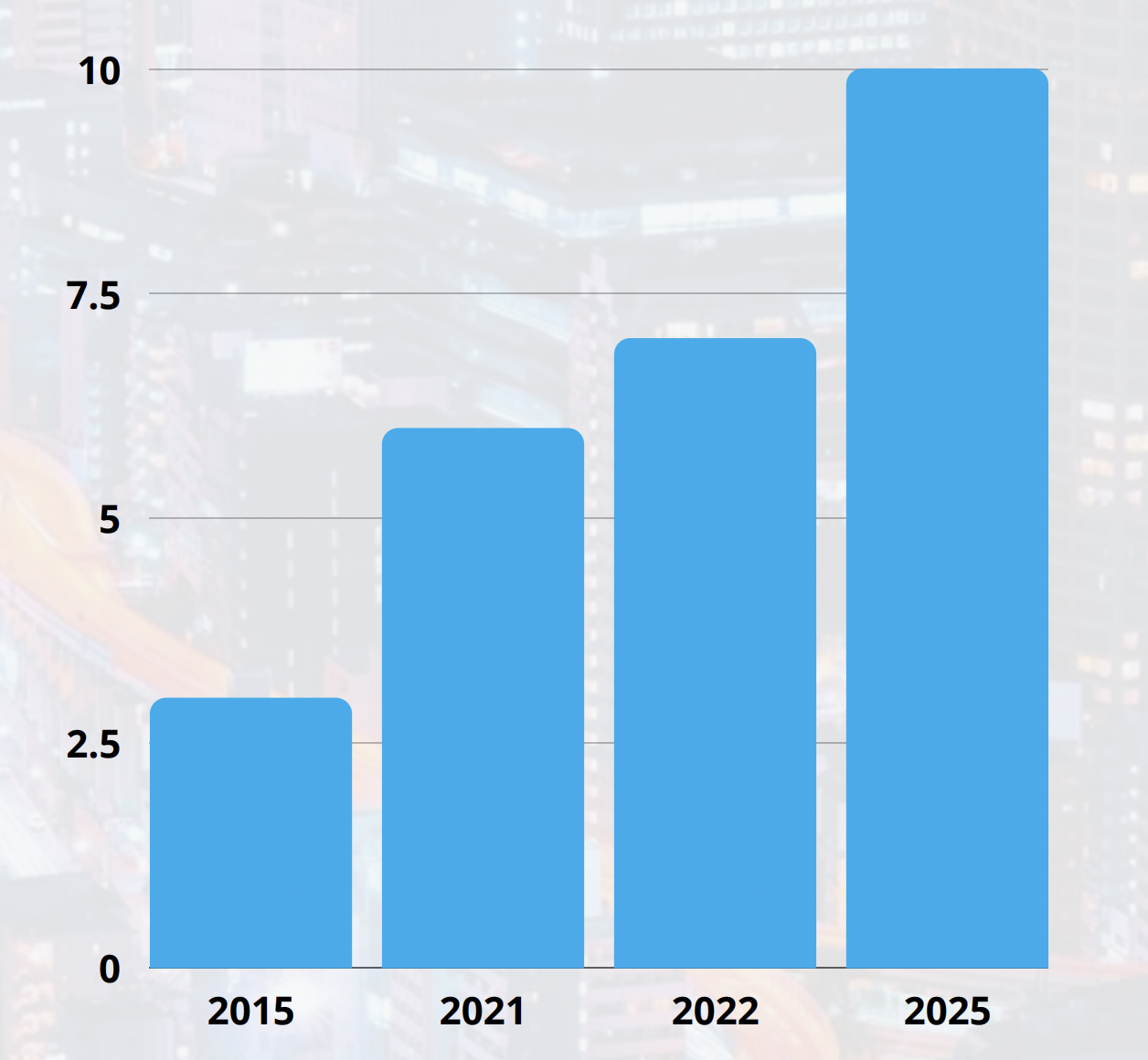
Cybercrime is predicted to cost the world $7 trillion USD in 2022. If it were measured as a country, then cybercrime would be the world’s third largest economy after the U.S. and China. —— Cybersecurity Ventures
Three Characteristics of Cybercriminals
Over the past 11 years, GeeTest has been at the forefront of the battle against cyber hackers. Through our ongoing efforts, it has been concluded that cybercrimes frequently exhibit the characteristics of being efficient, rapid, and operating on a huge scale, enabling them to quickly and effectively target and exploit vulnerabilities in organizations' networks and systems.
To achieve their goals, cyber hackers may employ a variety of tactics. Behavior-based attacks are a prevalent method used by hackers to carry out fraudulent activities. They may, for example, utilize automated tracking scripts to simulate the actions of real users, allowing them to bypass typical security barriers. This can be especially effective when combined with social engineering techniques like phishing or pretexting, which can trick even the savviest users into divulging their login credentials or other sensitive information.
They may also use device-based attacks, such as simulators, cloud control, group control, and API cracking programs, to carry out large-scale attacks simultaneously. This enables them to perform a range of fraudulent activities, including participating in vast numbers of marketing campaigns initiated by enterprises in order to generate bogus leads, get woolly party arbitrage, or steal valuable data.
Additionally, cyber hackers may use fake identities to remain undetected while carrying out their attacks. This could involve creating thousands of "throwaway" accounts to infiltrate and disrupt businesses. And these fake accounts can be used to spread disinformation, spam, or other malicious content, making it difficult for organizations to identify and defend against these threats.
The combination of high efficiency, fast speed, and large scale makes cyber hackers a formidable threat to organizations and enterprises.
How does GeeTest Increase The Cracking Costs?
Preventing all data breaches is an unrealistic goal as hacking technology is constantly evolving, making 100% comprehensive prevention practically unattainable. Instead, organizations should focus on discovering and minimizing their greatest risks.
Cybercrime cannot be eradicated, but the impact can be reduced. Bot management solution providers like GeeTest understand the importance of managing risk and creating the right mitigation strategies to achieve acceptable levels of risk for institutions. This implies continuously increasing the cost of cybercriminals to confront cyber attacks, which can assist lower enterprise operating costs. For instance, if a criminal could earn $100,000 by attacking a website but had to spend close to or even exceeding $100,000 to do so, they would typically not attack it. This is the core value of GeeTest's confrontation. GeeTest Adaptive CAPTCHA provides comprehensive risk mitigation strategies that can quadruple the costs of cybercriminals.

The Graph Convolutional Network (GCN) is a method for semi-supervised learning on graph-structured data. GeeTest, through the integration of the Graph Convolutional Network (GCN) technology, has upgraded its defense model to make the overall defense system intelligent and self-evolving. At the same time, GeeTest's neural network is expanding the depth of data mining and the breadth of security analysis to uncover the anomalies behind the source of problems more deeply.
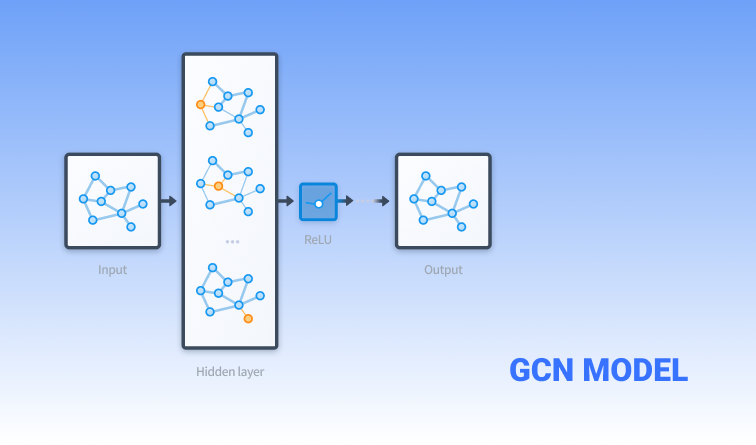
The GeeTest Security Lab has also applied fine-tuning and performance enhancement to the image recognition model through optimization techniques, while frequently updating and enhancing its verification image database with various security tactics, including IP frequency restrictions, Proof of Work (PoW), environment detection, and dynamic password. These measures not only ensure the reliability and efficiency of the verification process but also increase the cost for attackers to crack it.
- IP frequency restrictions
The GeeTest security system implements restrictions on the maximum frequency of visits and volume of traffic from specific source IP addresses within a designated time frame. This serves to safeguard against server overloading and the potential for denial of service (DoS) attacks.
- Proof of Work (PoW)
The GeeTest risk management system employs a Proof of Work (PoW) mechanism. By tailoring the PoW requirement to the individual risk level of each user, legitimate requests can be verified in a mere 10 milliseconds, while the PoW requirement is heightened for suspicious requests that consume excessive CPU resources.
- Network Environment Detection
GeeTest utilizes network behavior analysis to detect signs of bot activity, such as CAPTCHA farm activities, fluctuations in IP frequency, and web simulation, through the analysis of user interactions during the verification phase. This information is evaluated promptly to assess the risk level, making an immediate determination of whether the visit is authentic or requires restriction, thereby elevating the security and performance of the network.
- Dynamic Password
An advanced dynamic password authentication mechanism is implemented to prevent unauthorized access, as the password will become invalid after a set period, even if obtained by unauthorized authorities.
Final Thoughts
In the constantly changing landscape of cybersecurity, it is imperative for organizations to adopt a comprehensive approach to protect themselves against evolving threats. This requires a combination of reducing risk factors, elevating the cost of attack, and being adaptable to new challenges.
GeeTest offers CAPTCHA solutions that can be implemented at all crucial entry points such as login, password recovery, ordering, posting comments, checking out, and more, effectively combating attacks such as credential stuffing, account takeover, and gift card cracking. The deployment of CAPTCHAs not only adds an additional layer of security, but also makes it more challenging and costly for hackers to breach the system.
With GeeTest's advanced machine learning technology and expertise, organizations can gain a deeper understanding of their risks and implement more effective measures to enhance their security.
Try the GeeTest Adaptive CAPTCHA demo and claim a 30-day free trial.
Selvia Zheng
Marketing Specialist @ GeeTest
Subscribe to our newsletter