What Is Device Fingerprinting and How Does It Work in 2025
28 Jul 2025 • 10 min read
What Is Device Fingerprinting and How Does It Work in 2025
28 Jul 2025 • 10 min read
Device fingerprinting identifies and tracks individual devices by collecting unique attributes like hardware configurations, software versions, and network details to create a digital signature. In 2025, adoption has surged as traditional methods like cookies lose effectiveness against new privacy tools. Google's policy change now permits device fingerprinting, making it essential for security, fraud prevention, and privacy management.
Key Takeaways
- Device fingerprinting creates a unique digital ID by collecting hardware, software, and behavioral data from devices.
- It tracks users more persistently than cookies, working across browsers and devices even after clearing cookies.
- This technology helps prevent fraud, improve online security, and personalize user experiences effectively.
- Fingerprinting uses both passive data collection and active methods like canvas and WebGL fingerprinting for accuracy.
- Privacy concerns exist because fingerprinting is hard to detect and block, raising the need for transparency and consent.
- Regulations like GDPR and CCPA require companies to get user consent and protect fingerprinting data.
- Future trends include AI-driven fraud detection, advanced biometrics, and stronger privacy protections balancing security and user rights.
- GeeTest's solution minimizes private data use (e.g., IMEI/IDFA) through weak-feature attribution, generating stable tamper-resistant fingerprints.
Understanding Device Fingerprinting

Definition
Device fingerprinting is the process of collecting information about a device’s unique configuration—such as hardware specs, software versions, browser settings, and network protocols—to identify it. Even devices with the same model can vary slightly, creating distinct digital fingerprints. This technique is widely used in analytics, ad tracking, fraud prevention, and cybersecurity. Experts often describe it as building a digital profile that helps detect threats and monitor for suspicious behavior.
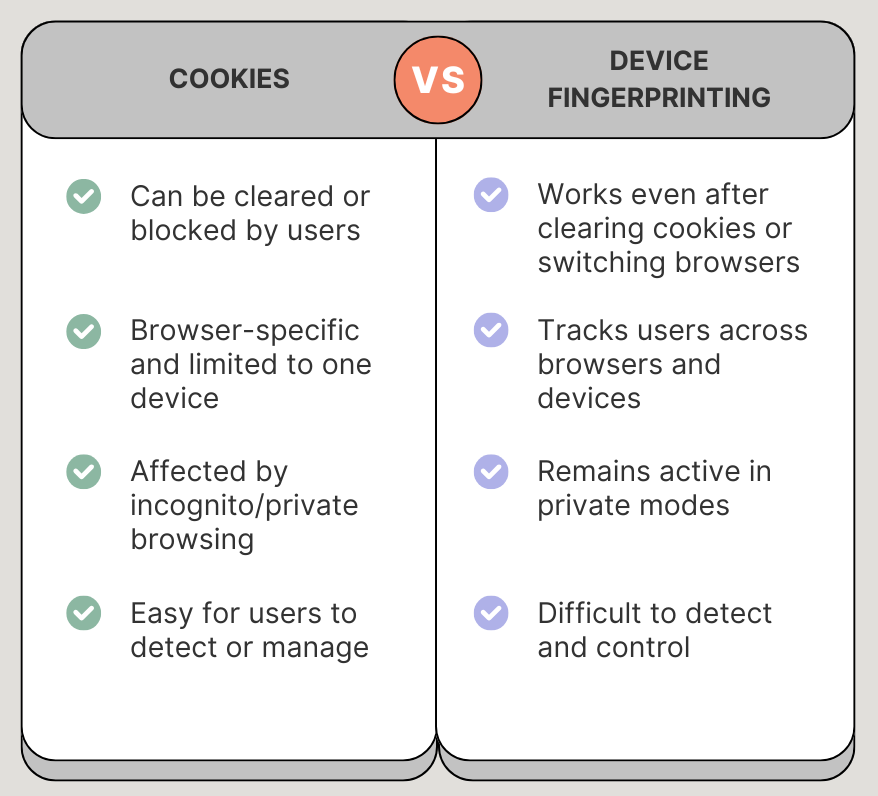
Comparison with Cookies
Unlike cookies, which store small files on a user’s device and can be easily deleted or blocked, device fingerprinting passively collects configuration data without storing anything locally. This makes it more persistent and harder to avoid. Even switching browsers or using private mode won’t prevent fingerprint-based tracking.
What Data Does Device Fingerprinting Collect?
Hardware Info
Device Type
Websites and applications often start by identifying the type of device in use. They check if the visitor uses a smartphone, tablet, laptop, or desktop. This information helps create a basic profile. Locally installed applications can access unique hardware identifiers such as MAC addresses and serial numbers. These identifiers play a critical role in distinguishing one device from another. Device make and model also provide valuable clues. For example, a server can recognize if a user connects with a Samsung Galaxy S24 or an Apple MacBook Pro. This level of detail supports accurate identification.
- Device make and model
- MAC address and serial number (when accessible)
- Device category (smartphone, tablet, laptop, desktop)
Screen Resolution
Screen resolution and pixel density tailor website layouts while enhancing fingerprint uniqueness. Advanced techniques like WebGL extract GPU details, and canvas fingerprinting detects hardware rendering variations.
- Screen width and height in pixels
- Pixel density and color depth
- Graphics card and driver details
- Canvas rendering characteristics
Software Details
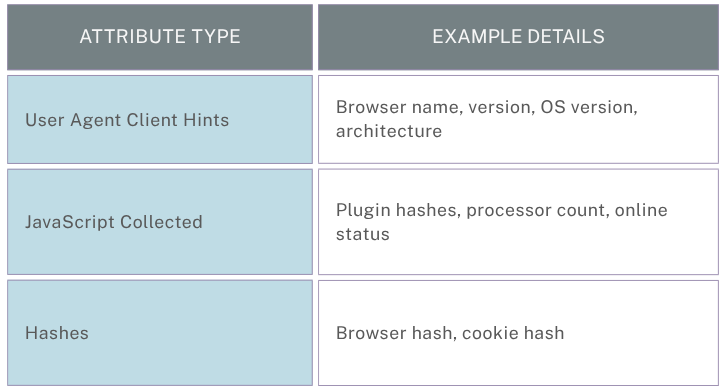
Browser
Browsers expose information through user agent strings and client hints, revealing details like version, platform, architecture, and bitness. JavaScript can also collect additional details such as installed plugins, number of processor cores, and network status—adding depth to the device’s software profile.
Operating System
The operating system adds another layer of data, including system name, OS version, and app-level specifications. In mobile environments, fingerprinting tools may also assess battery state or detect if a device is rooted or emulated.
- OS name and version
- Device system name
- Battery level and charging status
- Rooted or emulated status
Network Attributes
IP Address
IP addresses serve as a primary network identifier. They reveal the user’s approximate location and network provider. Both IPv4 and IPv6 addresses can be collected. Some systems also check for proxy types and network country codes. Persistent Naming Attributes (PNAs) rely on unique hardware characteristics, such as vendor, model name, and serial number, to maintain consistent device naming even after system changes.
- IPv4 and IPv6 addresses
- Proxy type and network country ISO
- Vendor, model, and serial number for stable identification
Timezone
Timezone settings help pinpoint a device’s geographic region. JavaScript can detect the time zone offset, which, when combined with other data, strengthens the fingerprint. This information proves useful for fraud detection and regional customization.
- Time zone offset
- Local time settings
Behavioral Data
Behavioral data adds a dynamic layer to device identification. Unlike static hardware or software details, behavioral patterns change over time and reflect how a person interacts with their device. These patterns are unique to each user, making them difficult to copy or fake.
Security systems now collect a wide range of behavioral biometrics to improve accuracy. Some of the most common types include:
- Keystroke dynamics: This measures how users type—including rhythm, typing speed, key pressure, and pause intervals. Each person has a unique typing signature.
- Mouse movement patterns: Systems track how users move their mouse—speed, direction, and acceleration—revealing subtle habits over time.
- Navigation behavior: Fingerprinting tools analyze how users scroll, click, or use keyboard shortcuts. These habits contribute to a unique interaction profile.
- Touch gestures: On mobile devices, gestures such as swiping, tapping, and pinching help differentiate users based on how they handle screens.
When combined with device-level data, these behavioral signals allow for highly accurate user profiling and fraud detection—even when users attempt to disguise their identity.
How Device Fingerprinting Works: The Technical Side
Passive Methods
Passive methods collect information from a device without direct interaction or noticeable prompts. These techniques rely on data that the device naturally sends during normal web browsing or network communication. Because passive methods do not require scripts or extra requests, they often go unnoticed by users.
Common passive data points include:
- IP address
- HTTP request headers
- User agent
- Screen resolution
- Operating system
- System language and country
- Device orientation
- Battery level
- Installed fonts and plugins
- System uptime
Websites and servers gather this information as soon as a device connects or loads a page. For example, the user agent string reveals browser and operating system details, while HTTP headers can show language preferences and device type. These data points help build a basic profile for each device.
Passive fingerprinting remains less intrusive and harder to detect. It does not require any special permissions or user actions. However, it usually provides less detailed information compared to active methods.
Active Methods
Active methods involve direct interaction with the device to collect more specific and detailed information. These techniques use scripts or network queries to ask the device for extra data. Users may notice these actions, especially if the browser requests permissions or runs visible scripts.
Some of the most common active data collection techniques include:
- Canvas fingerprinting: Uses the HTML5 canvas element to draw graphics and analyze rendering differences caused by browser, operating system, and hardware variations.
- WebGL fingerprinting: Renders 3D graphics using the WebGL API, capturing unique details tied to the device’s GPU and browser.
- TCP fingerprinting: Analyzes TCP/IP packet characteristics such as initial packet size, time-to-live (TTL), and flags to identify network stack behavior.
- Media device fingerprinting: Lists connected media devices and their IDs, though this often requires user permission.
- Audio fingerprinting: Examines how the device plays sound, using differences in browser versions and CPU architectures.
- Navigator interface queries: Extracts browser and operating system details from the user agent and navigator object.
- Touch event detection: Checks for touch support to distinguish between device types.
- Screen resolution checks: Verifies screen and window size for inconsistencies.
- Battery status checks: Monitors battery level to help separate real users from automated environments.
Active fingerprinting methods provide more detailed and accurate device profiles. However, they are more detectable and sometimes require user consent.
Identifier Creation
The process of creating a unique device identifier involves several steps. Each step collects and combines different types of data to form a digital fingerprint.
- Gather device information such as operating system type and version, browser details, installed plugins, screen resolution, and color depth.
- Collect browser information, including HTTP headers, user agent string, time zone, and language settings.
- Record hardware information like CPU and GPU capabilities, memory, storage, and battery status.
- Track behavioral data, such as mouse movements, keystrokes, or touchscreen interactions.
- Combine all collected data points into a single dataset.
- Use a cryptographic hashing algorithm, such as SHA-256, to generate a unique fingerprint from the dataset.
- Store only the hash, not the raw data, to help protect user privacy.
- Compare and monitor fingerprints over time to identify devices and detect changes.
This process ensures that each device receives a unique digital identity. The use of hashing helps keep the fingerprint secure and privacy-friendly.
In 2025, privacy-enhancing technologies (PETs) have become more common. These tools help manage and protect the data used in device fingerprinting. Google now allows fingerprinting again, citing PETs as a reason for improved privacy. Apple also requires app developers to declare their reasons for fingerprinting in privacy manifests. These changes aim to balance security needs with user privacy and transparency.
Real-World Applications of Device Fingerprinting
Security
Device fingerprinting plays a vital role in modern online security. Security systems use this technology to create a unique and persistent identifier for each device. This identifier relies on a combination of hardware and software attributes, making it more reliable than cookies or IP addresses. Security teams can detect fraud, prevent unauthorized access, and monitor suspicious activities by analyzing these fingerprints.
- Detects fraud and unauthorized access attempts
- Monitors for suspicious device behavior
- Reduces false positives in security alerts
- Supports compliance with privacy regulations like GDPR and CCPA
Many financial services and online platforms use device fingerprinting to enhance account security. For example, when a system detects an unfamiliar device or an anomaly in device behavior, it can trigger multi-factor authentication. Advanced solutions, such as those from GeeTest, use risk labeling and sophisticated algorithms to provide robust defense mechanisms. The persistence of device fingerprints across sessions allows security teams to spot anomalies and prevent account takeovers.
Fraud Prevention
Fraud prevention stands as one of the most important uses of device fingerprinting. Financial institutions and e-commerce platforms rely on this technology to identify suspicious device setups and unauthorized access attempts. By combining real-time digital footprinting, device intelligence, and AI-driven rules, companies can detect and block fraud before it happens.
Combining device fingerprinting with location intelligence makes fraud detection more resilient, even if a device resets or changes attributes.
Analytics
Analytics platforms use device fingerprinting to track user behavior across websites and apps. These platforms collect data such as operating system, browser type, screen resolution, installed fonts, plugins, and time zone. JavaScript-based techniques like canvas fingerprinting and user agent tracking help gather this information.
- Tracks user behavior across multiple sessions
- Builds detailed user profiles for a better experience
- Detects suspicious activities, such as multiple account creation
- Improves targeting for content and advertisements
Analytics providers combine these data points to create a unique device identifier. This identifier allows them to follow users even if they switch browsers or clear cookies. Device fingerprinting also helps detect fraud by identifying devices that create multiple accounts or engage in abnormal activity. However, privacy concerns remain, so analytics platforms must balance tracking with user consent and transparency.
Personalization
Personalization is a key benefit of modern web technology. Through device recognition, websites can identify users—even across browsers or after cookies are cleared—and deliver customized experiences. First-time visitors might see special offers, while returning users get personalized recommendations, reminders, or loyalty rewards.
By recognizing a user’s location or behavior, websites can adjust content automatically—like showing French to users in France or retargeting ads for products they viewed earlier. Unlike cookies, device-based recognition is harder to block, offering more persistent personalization.
Common uses include:
- Showing content in the user’s language
- Offering return-customer deals
- Reminding users of cart items
- Suggesting content based on browsing
- Supporting loyalty programs
Personalization creates smoother user experiences while boosting customer loyalty and business revenue.
Privacy Risks and Legal Considerations
Device Fingerprinting raises privacy concerns because it works invisibly and can track users across many websites. Companies use it for fraud prevention and targeted advertising, making it a powerful tool compared to cookies.
Privacy Concerns
Device fingerprinting raises significant privacy concerns in 2025. Many users worry about the persistence and invisibility of this tracking method. Unlike cookies, device fingerprinting creates identifiers that are difficult to block or erase. This persistence allows companies to track users across sessions, browsers, and even IP address changes, often without explicit consent.
- Google’s 2025 policy change, which loosened restrictions on fingerprinting, has increased privacy risks.
- The UK’s Information Commissioner’s Office (ICO) criticized fingerprinting as unfair tracking that reduces user choice and control.
- The ICO requires businesses to obtain prior consent and provide transparency about fingerprinting under UK GDPR.
- Fingerprinting now extends beyond fraud prevention to analytics and personalization, increasing the risk of misuse.
- Healthcare organizations face special risks, as fingerprinting can track patients and providers without consent, potentially violating HIPAA rules.
- Machine learning applied to fingerprint data can re-identify users, even when data is obfuscated.
Regulations
GDPR
The General Data Protection Regulation (GDPR) in the European Union treats device fingerprinting as processing of personal data. This means organizations must follow strict rules:
- Explicit user consent is required before collecting or processing fingerprinting data.
- Consent must be freely given, specific, informed, and unambiguous.
- Organizations must explain what data they collect, why they collect it, and how they use it.
- GDPR principles such as lawfulness, fairness, transparency, purpose limitation, data minimization, and security apply.
- Non-compliance can result in heavy fines and reputational damage.
GDPR does not mention device fingerprinting by name, but regulators consider it personal data processing because it can identify individuals directly or indirectly. Legitimate interest may apply for fraud prevention, but most marketing and analytics uses require consent.
CCPA
The California Consumer Privacy Act (CCPA) and its amendment, the California Privacy Rights Act (CPRA), regulate device fingerprinting in the United States. Under these laws:
- Device fingerprinting data is personal information if it can link to individuals or households.
- Businesses must provide clear notice and a conspicuous opt-out mechanism for consumers.
- Sharing fingerprinting data with third parties for advertising is considered a "sale," triggering disclosure and opt-out requirements.
- CPRA expands protections, requiring notification when sharing personal information and providing opt-out rights for sale or sharing.
- Cross-context behavioral advertising, which often uses fingerprinting, faces stricter rules.
Security vs. Rights
Device fingerprinting offers strong security benefits but also challenges user rights. Security teams use fingerprinting to:
- Create unique device IDs for accurate user identification.
- Detect suspicious activity and advanced fraud techniques.
- Prevent account takeovers and payment fraud.
- Distinguish between real users and bots.
- Enable adaptive security measures based on risk.
However, privacy advocates argue that fingerprinting tools often lack transparency and can act as black boxes. Users may not understand how their data is used or have control over it. Experts recommend moving toward privacy-preserving authentication methods, such as cryptographic keys, that respect user rights and provide clear consent.
Balancing security and privacy requires organizations to adopt transparent practices, obtain informed consent, and use privacy-enhancing technologies.
The Future of Device Fingerprinting in 2025 and Beyond
Digital identity and security are evolving rapidly, driven by AI, biometrics, and growing privacy concerns. Technology, regulation, and user expectations are shaping the next generation of solutions.
Technology Advancements
AI enhances real-time fraud detection through smarter risk scoring. Biometric systems—especially fingerprint tech—are expanding across devices and sectors. Privacy-preserving tools like differential privacy and zero-knowledge proofs enable secure data use without exposing identities.
Regulatory Shifts
Laws like GDPR and CCPA demand explicit user consent and limit data collection. Regulators are pushing privacy-first technologies, consent-based tracking, and transparent data practices. Fingerprinting is seen as a transitional method, with a shift toward privacy-centric models.
Market Growth & Challenges
By 2030, browser fingerprinting may reach $3.1 billion, and fingerprint access control $9.80 billion. Growth is fueled by cyber threats and demand for secure authentication. However, talent shortages and high costs may hinder adoption in some regions.
The future promises stronger security and privacy, powered by innovation and guided by robust legal frameworks.
Conclusion: The Balanced Future of Fingerprinting
Device fingerprinting in 2025 is no longer just a supporting tool—it’s a core technology for fraud prevention, security enforcement, and seamless personalization. As tracking techniques evolve and cookie-based methods become obsolete, fingerprinting offers persistent, cross-device identification that’s both scalable and precise.
Yet with this power comes responsibility. Organizations must navigate complex regulatory landscapes and growing user expectations around privacy. The key to ethical and effective fingerprinting lies in accuracy, transparency, and minimal reliance on sensitive data.
GeeTest Device Fingerprinting stands out as a next-generation solution that delivers on all fronts:
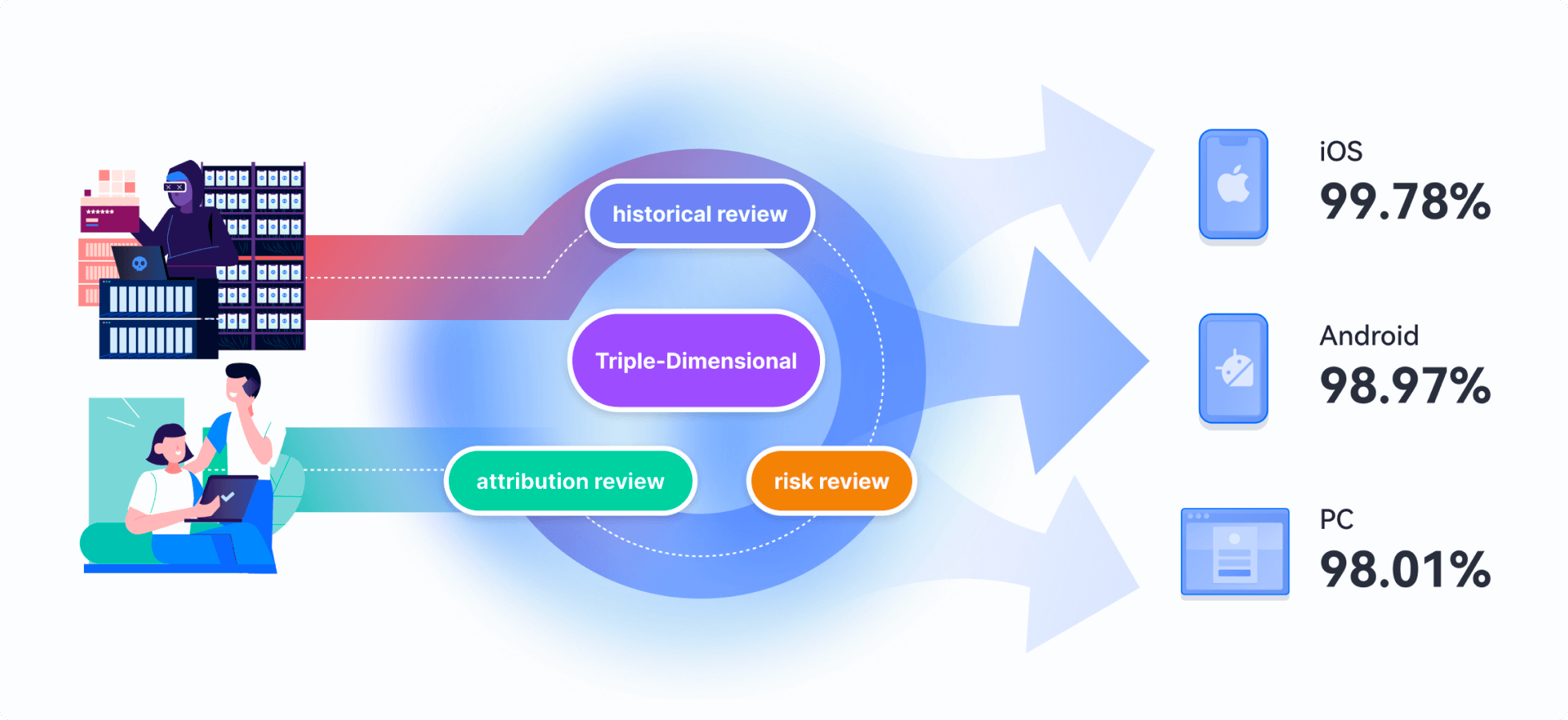
- High Accuracy: Its identification engine achieves impressive accuracy rates across platforms—iOS: 99.78%, Android: 98.97%, and Web: 98.01%—making it ideal for large-scale, real-time risk evaluation.
- Multi-Dimensional Risk Tagging: GeeTest analyzes both device signals and behavioral patterns to generate multi-layered risk labels. This enables advanced fraud detection, such as identifying bots, emulators, and malicious account farms.
- Account Deduplication & User Integrity: Through deep fingerprint correlation and real-time behavior analysis, GeeTest supports accurate account analysis and duplicate account detection, improving business intelligence and reducing abuse.
- Privacy-Respecting Architecture: By minimizing dependence on private identifiers like IMEI or IDFA, GeeTest aligns with modern privacy standards. Its fingerprinting model is designed to protect user anonymity while preserving detection performance.
In a landscape where both trust and risk are growing concerns, GeeTest offers a secure, privacy-conscious, and future-ready solution for businesses that take fraud seriously and respect user rights.
FAQ
What is device fingerprinting?
Device fingerprinting is a technique that collects hardware, software, network, and behavioral attributes from a device to create a unique identifier. Unlike cookies, it doesn’t store anything on the user’s device and is harder to block or erase.
How is device fingerprinting used in 2025?
In 2025, device fingerprinting is widely used for:
- Fraud prevention
- Account security
- Bot detection
- User personalization
- Behavioral analytics
It has become more accurate and privacy-aware thanks to AI and privacy-enhancing technologies.
Is device fingerprinting better than cookies?
Yes. Compared to cookies, fingerprinting:
- Tracks users across browsers and sessions
- Persists even in incognito or private mode
- Doesn’t rely on user-stored files (like cookies do)
- Is much harder to delete or evade
However, it also raises more serious privacy concerns, making transparency and consent essential.
What kind of data does device fingerprinting collect?
Device fingerprinting collects a wide range of data, including:
- Hardware: Device type, screen resolution, GPU, system fonts
- Software: Browser version, operating system, plugins, time zone
- Network: IP address, proxy detection, geolocation
- Behavioral: Keystroke patterns, mouse movement, navigation habits, touch gestures
Can device fingerprinting identify users personally?
Not directly. It doesn’t collect names, email addresses, or passwords. However, combining fingerprint data with other signals can re-identify users, especially over time. That’s why regulations like GDPR treat it as personal data.
Is device fingerprinting legal?
Yes, but with strict conditions. Under GDPR (EU) and CCPA/CPRA (California):
- Companies must obtain explicit consent if fingerprinting is used for tracking or personalization.
- Users must be informed about what data is collected and how it’s used.
- Fingerprinting for fraud prevention may qualify under legitimate interest, but marketing uses often require opt-in.
How accurate is modern device fingerprinting?
Modern fingerprinting solutions—especially those using behavioral signals and AI—can be highly accurate. For example, GeeTest Device Fingerprinting reaches:
- 99.78% accuracy on iOS
- 98.97% on Android
- 98.01% on Web platforms
This level of accuracy enables precise account detection, bot prevention, and behavioral risk analysis.
GeeTest
GeeTest
Subscribe to our newsletter