Gaming Safely: Arknights' Battle Against Bots with GeeTest CAPTCHA
22 Sep 2023 • 10 min read
Gaming Safely: Arknights' Battle Against Bots with GeeTest CAPTCHA
22 Sep 2023 • 10 min read
Online video games have transcended mere entertainment, evolving into a vast digital economy with hundreds of millions of global participants. As this market expands, it becomes an attractive target for malicious activities. Gaming account boosting, account sales, and deteriorating gaming experiences have become increasingly common. To ensure a secure gaming environment for players, Hypergryph, the developer of the tactical RPG/tower defense mobile game Arknights, has joined forces with GeeTest.
In 2019, Arknights emerged as a standout anime tower defense game, quickly gaining a leading position through innovative gameplay within its category. The game's appeal lies not only in its unique tower defense mechanics but also in its captivating storyline set in the fictional world of "Rhodes Island." Players take on the role of medical personnel, navigating through an intriguing narrative while facing in-game challenges. The introduction of elements like Roguelike and card gameplay has further enriched the gaming experience.
Arknights has made significant strides in both revenue and growth rankings, according to the 2023 Global Insights into Popular Mobile Gaming Genres report by SensorTower. However, this success has attracted malicious attacks, particularly profit-oriented activities like gaming account boosting and account sales. Gaming account boosting involves creating fake accounts to play the game, accumulate in-game assets, and then sell them for profit on third-party platforms. This unethical practice poses a significant threat to game developers and users.
.png)
Source: Sensor Tower
For popular and rapidly growing games like Arknights, profit-oriented activities such as gaming account boosting and account sales pose the most significant threats to game developers and users.
Gaming account boosting is an ongoing issue in the gaming market. Malicious actors employ a large number of fake accounts to play the game, aiming to obtain in-game currency, equipment, or other resources through mass registration and account boosting. They then trade these accounts for profit on third-party platforms. Rough estimates indicate that on a single platform, daily revenue from gaming account boosting exceeds approximately US$780,000.
This process primarily involves the following key steps:
- Massive account registration: Malicious actors typically use automated scripts to create a large number of fake gaming accounts.
- Account boosting: This step usually involves completing specific tasks and activities to increase the account's level, making it appear more authentic and avoiding detection as a fake account.
- Resource acquisition: Once the account is levelled up, malicious actors start using these accounts for illegal resource acquisition, cheating to obtain in-game currency, items, or other resources that they then illegally sell.
- Account for sale: After completing the previous steps, malicious actors sell these accounts to players or other stakeholders, often attracting buyers with their high levels, abundant resources, or rare items.
To combat these issues and maintain a fair gaming environment, Arknights and GeeTest collaborated to bolster account security. By implementing GeeTest CAPTCHA v4 during the login session, Arknights successfully thwarted malicious activities. Fake account registration and boosting attempts were intercepted, significantly reducing economic losses and ensuring a healthier ecosystem for the game and its players.
How GeeTest Helps
Since registering fake accounts is the first step in gaming account boosting, targeting account registration is vital. For added security, it is essential to intercept fake accounts during login sessions. In the registration and login pages, Arknights implemented GeeTest CAPTCHA v4, employing a variety of CAPTCHA challenge forms such as OneTap, Slide CAPTCHA, or Icon CAPTCHA based on the assessed account security level.
The application of GeeTest CAPTCHA in the Arknights login session has hindered profit generation for malicious actors by obstructing their malicious activities. However, they are no longer limited to registering accounts or boosting them manually; bad actors now attempt to bypass CAPTCHAs. Based on years of experience in the battle against bad bots, GeeTest has identified two methods employed by bots to crack CAPTCHAs: web simulator cracking and API protocol cracking.

CAPTCHA bypass methods
Web simulator cracking: GeeTest possesses the capability to recognize and counter common web simulators, distinguishing them from regular browsers. It can precisely identify various web simulators like PhantomJS, Nightmare, Chrome-driver-driven emulators, Selenium-driven emulators, and Headless emulators, among others.
API protocol cracking: GeeTest's client-side verification includes JS code obfuscation and parameter encryption, offering a defense against a majority of scripts. Malicious actors seeking to crack the CAPTCHA need to first decipher the client-side obfuscated code and parameter encryption.
By utilizing these technologies, GeeTest effectively mitigates over 98.5% of cracking attacks from sophisticated bots. Besides enhancing CAPTCHA security by countering these cracking methods, GeeTest provides Hypergryph with a customized CAPTCHA image album to ensure a consistent appearance and user interface for the CAPTCHA, offering a unified brand experience. Hypergryph can manage uploaded image sets through the GeeTest dashboard, enabling resource switching for different scenarios and CAPTCHA challenges.
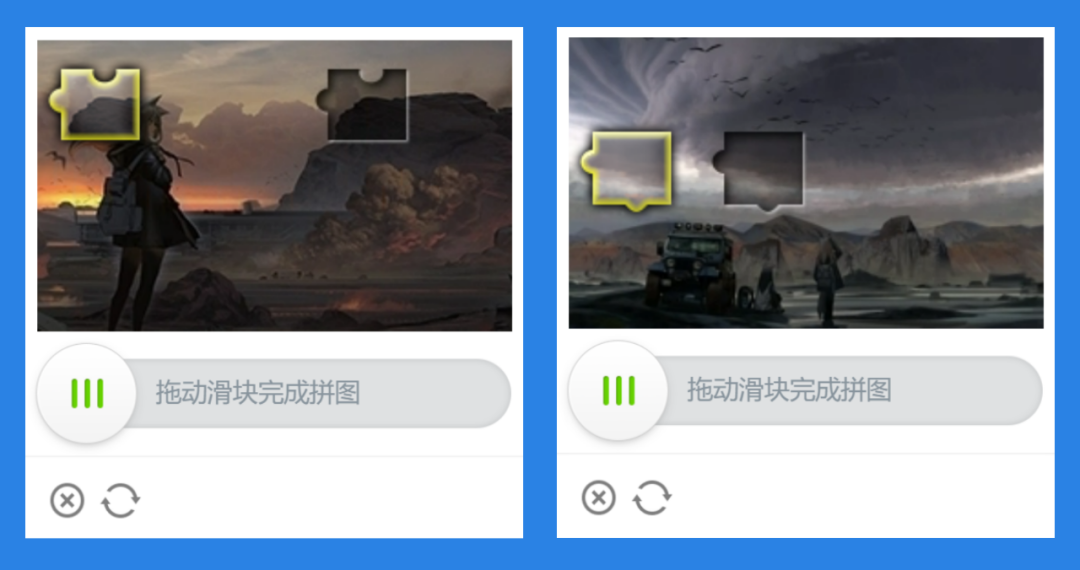
Customized CAPTCHA image for Arknights
In essence, GeeTest CAPTCHA has not only bolstered Arknights' security but has also effectively mitigated gaming account boosting and account-for-sale activities. This collaborative effort has not only reduced economic losses for Hypergryph but has also showcased its commitment to game quality, player rights, and a competitive edge in the gaming market.

Hayley Hong
Content Marketing @ GeeTest
Subscribe to our newsletter
