11 Best CAPTCHA Alternatives to Improve User Experience in 2025
21 Mar 2025 • 10 min read
11 Best CAPTCHA Alternatives to Improve User Experience in 2025
21 Mar 2025 • 10 min read
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) has been widely used to prevent automated bots from spamming your favorite online services. However, traditional CAPTCHA methods, such as distorted text or image selection, often frustrate users and negatively impact conversion rates.
The good news is that there are smarter alternatives that offer better security and a seamless user experience. This article will explore the top 11 CAPTCHA alternatives, categorized based on their interaction methods, and how they can help protect your website or apps from bots without annoying real users.
Passive CAPTCHA Alternatives (No User Interaction Required)
1. Honeypot Technique
Honeypot involves adding a hidden field (e.g., via CSS display:none or input[type=hidden]) in forms that normal users cannot see but bots will attempt to fill it. If this field is filled, the submission is flagged as spam. This method's commonly used cases include:
- Contact forms
- Registration pages
- Comment sections
✅ Pros:
- Invisible to legitimate users (when properly implemented)
- No impact on user experience
- Easy to implement with minimal resources
❌ Cons:
- Less effective against advanced bots that detect honeypots
- Cannot be used as the sole security measure for high-risk application
- Potential accessibility issues if labels are not hidden properly
2. Time-Based Challenges
This method monitors the duration between form rendering and submission. Humans typically take 3-15 seconds to complete fields, while basic bots submit near-instantly. Common use cases include:
- Login forms
- Sign-up processes
- Payment verification pages
✅ Pros:
- No extra steps for users
- Effectively blocks basic automated bots
- Does not disrupt user experience
❌ Cons:
- Advanced bots simulate human delays at random intervals
- Auto-fill tools (e.g., LastPass) may trigger false positives
- Network latency can cause misidentification
- Requires continuous adjustment of time thresholds
3. Behavioral Analysis
This approach tracks user behavior such as mouse movements, scrolling patterns, and keystrokes to differentiate between bots and real users. Common use cases include:
- Fraud prevention systems
- Bot mitigation systems
- High-risk transaction verification
✅ Pros:
- Non-intrusive and seamless
- Highly effective against bots
- Can be integrated with machine learning for enhanced security
❌ Cons:
- Requires JavaScript and user-tracking (disableable by privacy tools)
- Potential privacy concerns due to behavioral data collection
4. ReCAPTCHA v3
Google’s ReCAPTCHA v3 assigns a risk score (0.1-1.0) based on user interactions with the website. A lower score means a user is likely a bot, and the site can take appropriate actions. Core applications include:
- Login authentication systems
- E-commerce checkout flows
- High-risk form submissions
✅ Pros:
- Fully automated and frictionless for users
- High accuracy with Google’s AI
- Well-integrated with Google’s ecosystem
❌ Cons:
- Privacy concerns with Google collects data across sites
- Can misclassify some legitimate users (like VPN/Tor users)
- Users still need a lot of analysis and configuration to set accurate thresholds
Light-Interaction CAPTCHA Alternatives (Minimal User Effort)
5. No-CAPTCHA Solutions
This next-generation approach eliminates explicit user interactions by analyzing behavioral patterns, browser telemetry, and AI-driven threat detection to verify authenticity. Designed for platforms prioritizing seamless user experience while maintaining robust security. Leading No-CAPTCHA technologies include:
- Google Invisible ReCAPTCHA: Leverages Google’s proprietary behavioral analysis engine and cross-site tracking.
- Cloudflare Turnstile: Uses a combination of browser telemetry and AI to verify users without requiring any input.
- GeeTest OneTap: Just a simple click to verify each visit to your website or app with security and data privacy not being compromised at all.
✅ Pros:
- Almost zero user interaction required
- Machine learning-powered threat detection (evolves with attack patterns)
- Dramatically reduces UX friction and form abandonment
- Lightweight SDKs with multi-platform compatibility (web, iOS, Android)
❌ Cons:
- May require additional integration effort
- Limited transparency into verification logic (black-box systems)
- Potential false positives in privacy-focused browsers (Tor/Brave)
6. Slider CAPTCHA
This method requires users to drag a slider to complete a puzzle, verifying their humanity. Slider CAPTCHA Widely was adopted in China and growing globally, it is particularly prevalent in banking and e-commerce sectors. Common use cases include:
- Secure banking transactions
- E-commerce checkout processes
- Mobile payment authentication
✅ Pros:
- Simple and gamified user experience
- Difficult for bots to bypass
- Cross-device compatibility (works on most browsers and platforms)
❌ Cons:
- Requires JavaScript execution
7. Math or Logic Questions
This method presents users with simple arithmetic or logic problems (e.g., “What is 3 + 7?”) as an alternative to traditional CAPTCHA systems. Common use cases include:
- Forum registrations and comment moderation
- Blog post interactions
- Educational platform assessments
- Low-security authentication workflows
✅ Pros:
- Minimal cognitive load for most human users
- Functions without JavaScript dependency (enhances accessibility)
- Customizable difficulty levels for adaptive security
- Language-agnostic implementation
❌ Cons:
- Susceptible to OCR tools and AI-powered solvers
- Creates barriers for users with dyscalculia or cognitive impairments
- Limited effectiveness against persistent attackers
- May reduce perceived professionalism for commercial applications
Identity-Based Verification (Supplement for Security )
8. Device Fingerprinting
Device Fingerprinting constructs a unique device identifier by analyzing hardware/software attributes (e.g., GPU specifications, font stack, canvas rendering, audio APIs) to detect anomalies. Deployed as part of layered security strategies, its common use cases include:
- Fraudulent transaction pattern detection (e.g., credential stuffing, carding)
- Multi-account abuse prevention in fintech platforms
- Session hijacking detection for enterprise VPN access
- Ad-fraud mitigation in programmatic advertising ecosystems
✅ Pros:
- High accuracy in identifying and tracking malicious activities
- Works without requiring user interaction
- Can detect sophisticated bots using multiple devices
- Detects device-spoofing bots through hardware incongruities (e.g., virtualized GPU drivers)
❌ Cons:
- Privacy concerns due to data collection (e.g., Evercookie persistence, canvas fingerprinting)
- Reduced efficacy in privacy-first browsers (Brave/Tor) with anti-fingerprinting defenses
- Can sometimes generate false positives
9. Email or SMS Verification
This authentication method delivers time-bound cryptographic codes (e.g., TOTP, HOTP) via email or SMS to validate user identity. Deployed as a foundational layer in multi-factor authentication frameworks, it balances accessibility with security for mainstream applications. Common use cases include:
- Two-factor authentication (2FA) for account logins
- Cryptographic key exchange confirmations (e.g., PGP email verification)
- High-risk transaction approvals (e.g., bank wire confirmations)
- Device pairing workflows (e.g., IoT device registration)
- Password reset authorization loops
✅ Pros:
- High security and widely accepted
- Works even when JavaScript is disabled
- Adds an extra layer of protection
❌ Cons:
- Email provider dependency (compromised IMAP access bypasses security)
- Privacy concerns under GDPR (phone numbers as quasi-identifiers) and telecom regulations
- Phishing susceptibility via fake verification code interceptors (e.g., Evilginx proxies)
- Usability friction from network delays (SMS delivery latency, email server queues)
10. OAuth-Based Login (Google/Facebook Login)
Instead of using CAPTCHA, websites can allow users to log in via trusted providers like Google, Facebook, or Apple. Designed for platforms aiming to balance security with conversion rate optimization, it replaces traditional CAPTCHA with delegated authentication workflows. Common use cases include:
- Consumer-facing SaaS application onboarding (e.g., Canva, Notion)
- Social media platform cross-posting integrations (e.g., Twitter/X embeds)
- Progressive web apps requiring minimal registration friction
✅ Pros:
- Enhances security and user experience
- Reduces form abandonment rates
- Minimizes spam registrations
❌ Cons:
- Account correlation risks
- Requires third-party authentication setup
- B2B/enterprise adoption barriers
- Not all users have accounts with major providers
11. WebAuthn (Biometric Authentication)
WebAuthn enables users to authenticate via biometric methods like fingerprint or facial recognition. This is commonly used in banking and enterprise security applications.
✅ Pros:
- Highly secure and convenient
- Phishing-resistant
- Do not rely on passwords
❌ Cons:
- Limited adoption across websites
- Requires biometric-enabled devices
Balancing Security and User Experience with GeeTest Bot Management Platform
There is no single tool that can perfectly balance security and user experience while addressing all cybersecurity challenges. Businesses need to select and deploy the most suitable security solutions based on their specific needs.
Many comprehensive security systems on the market today are prohibitively expensive, requiring significant integration and learning costs. This complexity often creates friction between IT administrators and business teams, making it difficult to implement security measures without disrupting operations. This is precisely where GeeTest Bot Management Platform stands out—delivering robust security while maintaining ease of use and seamless integration.
GeeTest Adaptive CAPTCHA: More Than CAPTCHA
As the 4th generation of GeeTest CAPTCHA, GeeTest Adaptive CAPTCHA is designed to provide both top-tier security and an effortless user experience. It integrates Honeypot, Behavioral Analysis, AI-powered Risk Detection, and more to effectively counter advanced bot attacks.
Unlike traditional CAPTCHA methods, GeeTest Adaptive CAPTCHA offers multiple verification modes—including invisible CAPTCHA, slider, icon, and gobang CAPTCHA—to minimize user friction.
Powered by machine learning algorithms, GeeTest Adaptive CAPTCHA continuously evolves, dynamically adjusting its security strategies before attackers adapt. With over 12 years of expertise in cybersecurity, GeeTest Adaptive CAPTCHA is no longer just a CAPTCHA—it is a comprehensive bot management solution that fortifies online platforms against malicious automation.
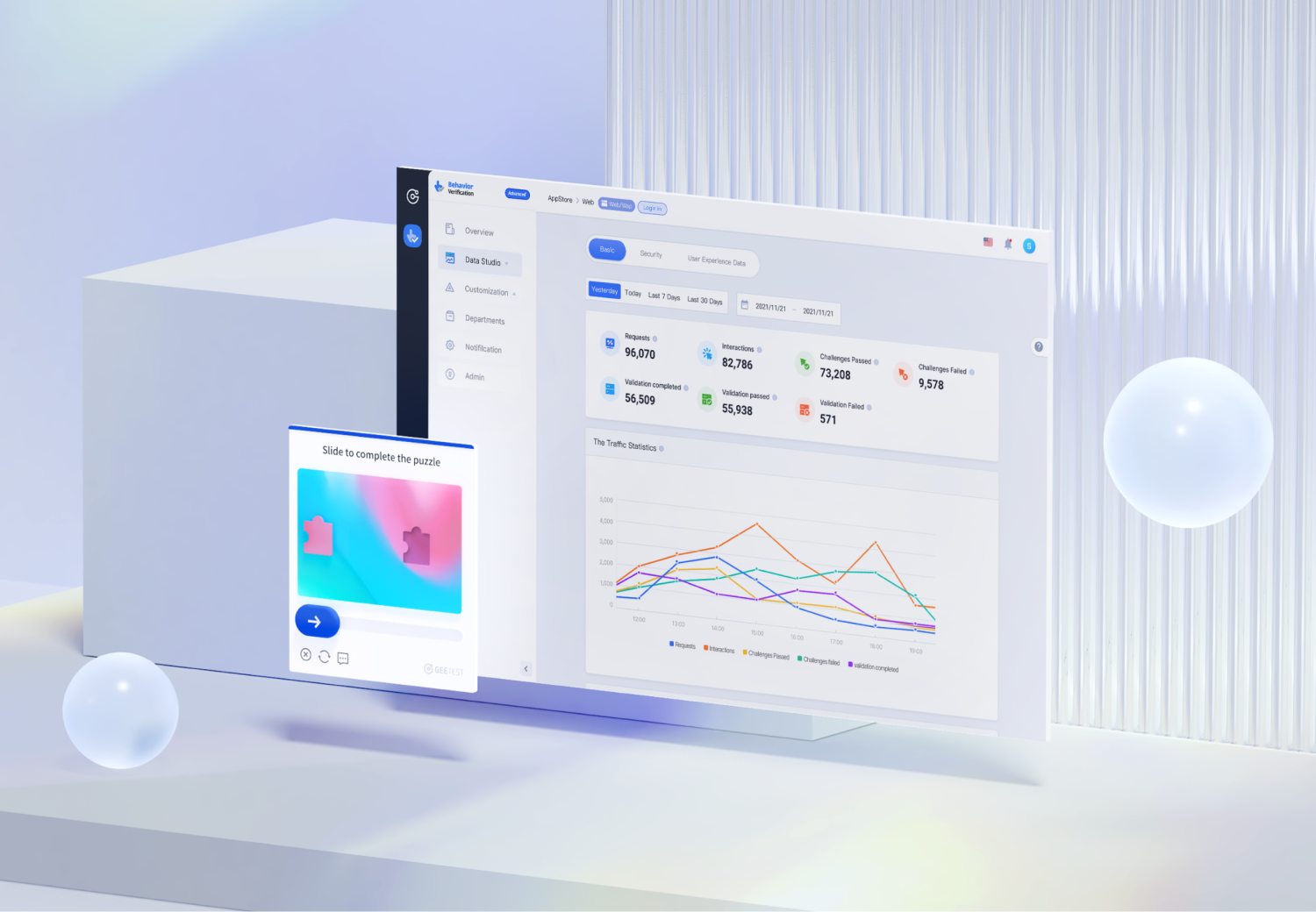
GeeTest Device Fingerprinting: Revolutionize device recognition
GeeTest Device Fingerprinting sets a new standard for accurate tracking and fraud detection. By analyzing multiple risk dimensions, it provides a holistic view of traffic patterns, allowing businesses to perform precise account analysis, deduplication, and fraud prevention.
Unlike traditional device tracking methods that rely on personal identifiers such as IMEI or IDFA, GeeTest Device Fingerprinting enhances privacy while maintaining high accuracy. This technology helps businesses detect fraudulent activities, prevent multi-account abuse, and strengthen security postures without compromising user privacy.
Conclusion
As automated threats evolve, outdated CAPTCHA methods are no longer sufficient to combat modern bot attacks. Fortunately, GeeTest Bot Management Platform provides a next-generation, AI-driven security solution that eliminates unnecessary friction while maintaining industry-leading protection.
Ready to safeguard your website with cutting-edge bot protection? Get started with GeeTest and try our demo today!
GeeTest
GeeTest
Subscribe to our newsletter